The Detailed Steps For Generating An Ssh Key
- The Detailed Steps For Generating An Ssh Key In Windows 7
- The Detailed Steps For Generating An Ssh Key Online
- How to Generate SSH Keys on PuTTY. SSH keys are one of the most secure SSH authentication options. It is definitely more secure than the usual SSH password authentication. Therefore, it is highly recommended to use SSH Key authentication method for connections to your servers.
- Generating SSH Keys for SFTP Adapters - Type 2. Describe the steps to create SSH key pairs which can be used as an alternative for password based authention.
- Detailed Steps on how to create ssh keys in Lunix. This contains details steps on how to create your ssh key pairs and load them onto your servers. Setting up SSH Keys (public and private key) Just a quick summary on how to use the ssh-agent so we can use ssh keys which are password protected. CLIENT “Main client your connecting from, holds.
Oct 17, 2011 The SSH client feature is an application running over the SSH protocol to provide device authentication and encryption. The SSH client enables a Cisco Nexus 3000 Series switch to make a secure, encrypted connection to another Cisco Nexus 3000 Series switch or to any other device running an SSH server. This connection provides an outbound connection that is encrypted.
3min Read
SSH keys are one of the most secure SSH authentication options. It is definitely more secure than the usual SSH password authentication. Therefore, it is highly recommended to use SSH Key authentication method for connections to your servers.
With password authentication, you can connect to your server from any location, you only need to fill in your password. However, if your password gets leaked, it is a major risk as anyone who knows your password will be able to get into the server.
SSH Key authentication only allows connections from clients whose key matches the one on the server. Basically, you generate a key pair (private key and public key). The private key is placed on your local machine and the public key is uploaded to the server. When connecting to the server, a validation of these two keys is made and if the key pair passes the validation you are allowed to connect. Of course, you can upload keys of multiple users so that you or other authorized users would be able to connect to the server from different computers.
As you can see this is a much safer connection method. In this tutorial, we will focus on Windows users who use PuTTY for connections to the server and show how to generate PuTTYSSH Keys. If you want to generate SSH Keys on Linux or Mac, see this tutorial.
What you’ll need
Before you begin this guide you’ll need the following:
- Access to your Linux server / VPS
- PuTTY and PuTTYgen installed on your computer (Download here)
Step 1 — Downloading PuTTYgen
Most of you have PuTTY installed on your computers already, however, to generate SSH Keys you also will need PuTTYgen.
- Download PuTTYgenhere
- You should be able to see this file downloaded:
No installation is required for PuTTYgen, it will run when you execute the file.
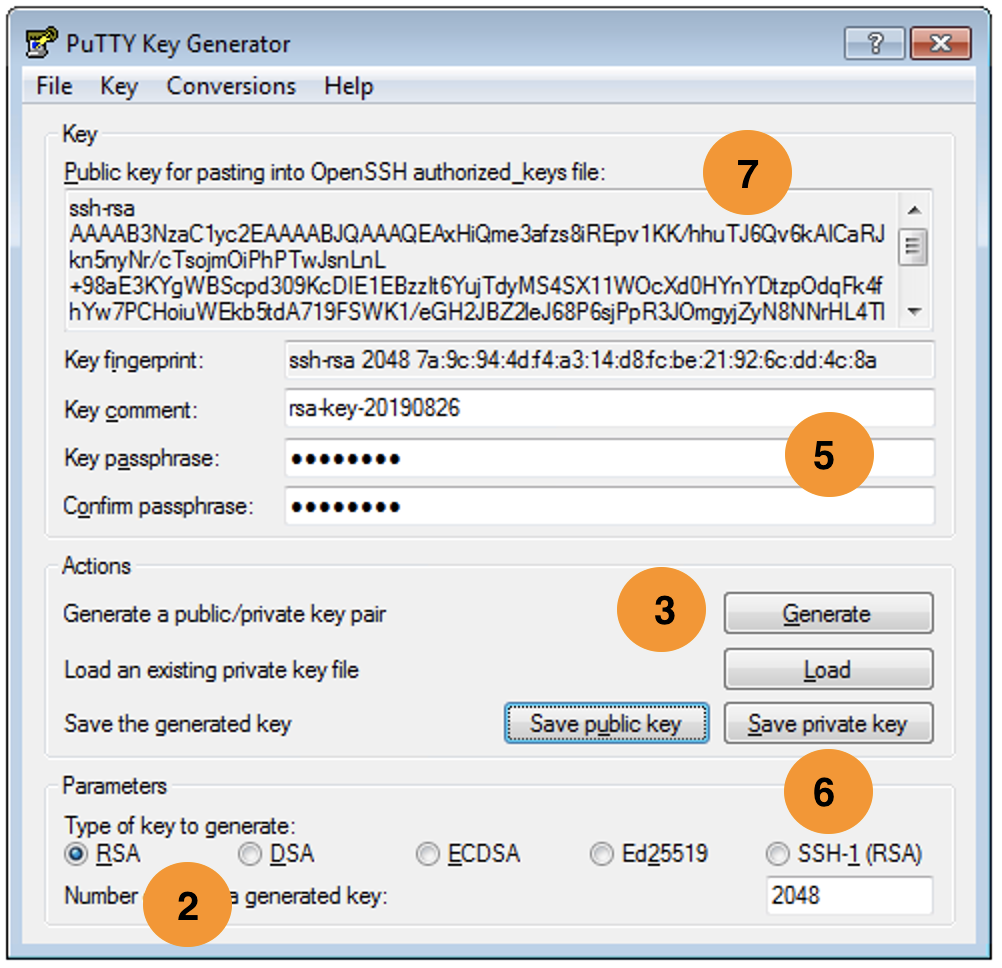
Step 2 — Generating your SSH Key pair
- Open up PuTTYgen by double clicking on the puttygen.exe file you have downloaded in Step 1.
- You should be able to see a window like this:
- Before generating your SSH Key pair, you can edit some settings, for example, key length, however, in most cases the default options will work just fine.
- Generate your SSH Key pair by clicking the Generate button.
- When the progress bar starts loading, move your mouse randomly across the area to load up the bar and generate your key pair.
- Your public SSH key will be displayed on the screen:
- For additional security it is highly recommended to think of a passphrase for your SSH key (However, you can also leave it empty):
- Save your private key to any desired location on your computer and name it anything you like.
- Save your public key to the same location on your computer and name it anything you like.
And that is it, you have generated your SSH Key pair. The private key will stay on your computer (do not provide it to anyone) while your public key needs to be uploaded to the server you wish to connect to.
Step 3 — Setting up your private key on PuTTY
In order for the server to recognize your computer when connecting from PuTTY, you need to attach the private key to PuTTY.
- Open up PuTTY.
- Navigate to Connection -> SSH -> Auth in the left sidebar.
- Browse for your private key file in the field Private key for authentication
- Select the private key file with .ppk ending and click Open.
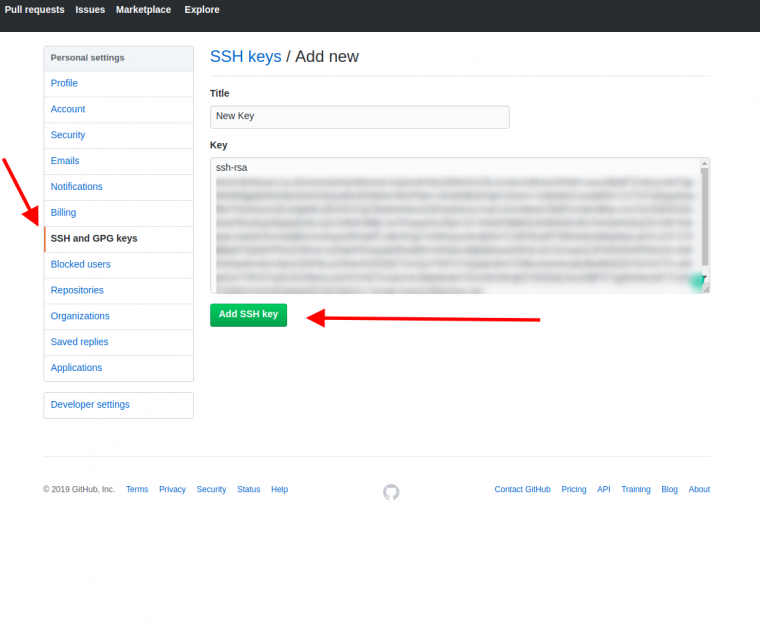
Step 4 – Adding public key to server
Lastly, you need to upload your public key to the server:
- On your local computer, open public key file (id_rsa.pub) you generated in Step 2 with any text editor and copy its contents (public key).
- Connect to your VPS using Putty. See this guide for detailed steps.
- If .ssh folder does not exist, create it together with authorized_keys file with the following command:
mkdir ~/.ssh touch ~/.ssh/authorized_keys - Secure SSH Key file by changing permissions:
chmod 0700 ~/.ssh; chmod 0644 ~/.ssh/authorized_keys - Open authorized_keys file with vim text editor:
vim ~/.ssh/authorized_keys - Press i key on your keyboard and right mouse button to paste the public key.
- Press Esc button and type in
:x, hit Enter button. This command will save changes made to the file.
That is it, you can now use SSH keys instead of SSH password authentication to connect to your VPS.
Conclusion
You have learned how to generate PuTTY SSH Keys using PuTTYgen. This will make your connection to the server a lot more secure and convenient as you will not need to fill in the password each time. We recommend using this way of SSH authentication at all times and disable password authentication for good to completely secure your server. To find out how to completely disable SSH Password authentication on your server and use SSH Key authentication instead, follow this tutorial: How to disable SSH Password authentication on VPS.
So a single point of reference for generating SSH keys is Generating SSH Keys for SFTP Adapters – Type 1 – Process Integration – SCN Wiki.
Recent observations from multiple projects where people create SSH public key and give to SFTP server team and mysteriously it connect then. It all left me searching here and there solve the problem. The causes of this are –
1. SAP PI Developer not aware whether keys are valid or not?
2. SFTP server administrator may just believe key provided are correct?
3. Basis team may not may also be unaware how the end ssh key should be? Is it uploaded at the correct place? Are the permissions correct.
So here I am, making an attempt to bridge the gap and provide you the “KEY for Key Generation”. Let us first know what all we may need, the so called –
Â
PRE-REQUISITES
1. WinScp (you may have other tools, but this one is simple and easily available 🙂 )
2. Cygwin installed with openSSH and openSSL packages
Video – https://www.youtube.com/watch?v=hh-V6el8Oxk
              Text – Installing Cygwin/X
3. Putty (FAMOUS) – this and WinScp can be combined.
4. NWA keystore access to create keystores
The above is enough to generate the keys and have it ready for the development. But, we PI consultants end up getting erroneous results for a new configuration. So to make sure we give the tested keys to client here is a tutorial to create the SFTP server on your local windows machine.
Apart from the links in the Part2, I will explain hand-picked steps out of the tutorial to set up sftp server correctly and quickly in the first attempt ( 😉 ) . So enough of reading let us start with the configuration.
1. Start Winscp -> Click on Tools -> Run PuTTygen
2. Select Parameters – SSH-2 RSA and Enter number of bits -2048. Click Generate.
3. Now you need to save the PrivateKey (ppk), PublicKey and PublicKey to be saved in SFTP server.
Note- i) The public key saved from “Save Public Key” and the “Public Key” to be saved in SFTP server can’t be same. The public key                                        saved starts with —- BEGIN SSH2 PUBLIC KEY —-, but the key to be pasted in SFTP server starts with ssh-rsa.
 ii) In the file authorized_keys, each line refers to a separate public key. So we also need to make sure there are no new line                                              characters in our key. So an authorized_keys file will look as below-
Â
4. Below are the Keys generated. Please follow the instruction in screenshots carefully.
Once the keys are generated, click on Save Private Key, Save Public Key and copy paste the key to be pasted in authorized_keys file and save.
Now, you will have 3 files generated. PPK private key, SSH public Key, SSH Public key to be pasted on to SFTP server. I have named 3 files as privateKey_SFTP.ppk, publicKey_SFTP.pub and publicKey_SSH.pub. Files will look as below.
5.Now sendpublicKey_SSH.pub file to SFTP server team to install via mail. If you want to test it with a local SFTP server, refer part 2 or video link embedded above.
Â
6. Before we put the key to SAP PO NWA KeyStore we must make sure our keys are set up correctly. To test this we can use WinScp or PuTTy.
Â
Testing With WinScp
Â
Â
Pc cleaner pro license key. In Advanced->Click Authentication under SSH -> Select the ppk private key
Â
Â
Â
Â
When you login for the first time, you will get a warning with the server’s fingerprint. This is a good sign showing it is able to reach the SFTP server. Just click Yes.
Â
Â
If you have chosen Passphrase while generating the key it will ask the passphrase else it will connect.
Â
And that is it, you will be placed at the SFTProot folder.
Â
Â
This must be your Hurray! moment. After this the task is easy. We need to convert PPK to PKCS12 and import in NWA. Lets see how to do that too.
Â
6. Now we need to convert privateKey_SFTP.ppk to pkcs12 format for SAP PO to import in NWA key store. For this Cygwin must be installed with openssl package
Â
  i) We will generate a PEM private key. I am naming it as privateKey_SFTP.pem. So again launch WinSCP->Tools->Run PuttYgen
  ii) Click on File->Load Private Key and choose your PPK key (privateKey_SFTP.ppk)
Â
  Â
      iii) Once the key is loaded, I recommend remove the passphrase this time and click Conversions->Export Open SSH Key, it will give warnign for blank passphrase. Just click YES and proceed. Name it as <yourname>.pem (privateKey_SFTP.pem)
Â
It will look like
Â
Â
    iv) Now launch cygwin as administrator . Right click -> run as administrator. Now run change directory ( cd) command to move to directory where you kept you pem file. for the ease place it in any drve G: , D: . This will save us to struggle with CD command 😉
v) use OpenSSL package commands to create X.509 certificate
    openssl req -new-x509 -days 3650-key privateKey_SFTP.pem -out x509_certificateSFTP.pem
Â
Â
Â
      Â
Â
                v) Now we will create PKCS 12 key to be imported in NWA with a password. Continuing in the CYGWIN enter following command
Â
            openssl pkcs12 -export -in x509_certificateSFTP.pem -inkey privateKey_SFTP.pem -out sftp_keystore.p12
Â
Â
Â
7. Now login to NWA of SAP PO/PI . http://<host>:<port>/nwa…… Configuration->Certificates and keys
Â
      i) Click on Add View-> Give View Name
Â
       ii) choose SFTP_KeyStore -> Import Entry-> PKCS#12 and click choose file to select the p12 generated. Provide the password which we set in cygwin while generating P12 and click import
Â
Â
Â
Â
This is all. Now you can select the above private key in your SFTP channel and continue with your development.
Â
Â
In the Part 2, I will show how to test the connection with PuTTy (already shown with WinScp) and also how to set up the local SFTP server. Stay Tuned for Part2
The Detailed Steps For Generating An Ssh Key In Windows 7
Â
The Detailed Steps For Generating An Ssh Key Online
Â
