Set Length Hash Key Generator Sql Server
Apr 09, 2016 For instance a customer with code NL123 will have the same hash key on all distributed parts of the data warehouse. Because the hash key always has the same length and is stored as a (fixed length) CHAR column, performance is usually better than when the business key column(s) are directly used as primary key. How to calculate a hash difference in T-SQL. Encryption brings data into a state which cannot be interpreted by anyone who does not have access to the decryption key, password, or certificates. Hashing brings a string of characters of arbitrary size into a usually shorter fixed-length value or key. Read on to learn about hashing in SQL Server and how it is different from encryption.
- Sql Server Hash Column
- Sql Server Hash Function
- Sql Server Hash Password
- Set Length Hash Key Generator Sql Server 2017
A few days back, I was working with one of our partners who had a requirement of creating a SSL self-signed certificate through MMC console. As we are already aware that it is a complex and a tedious procedure, tried developing a script to ease the task for us. Also found that there were a lot of partners asking for assistance in having a script based approach to create the certificates.
Tried finding a way out by looking through various discussion forums which yielded nothing, but queries to build a script to accomplish the task. Addressing this requirement of the partner pool, here is the blog explaining the script based way of creating the Self-signed certificates and registering them meeting the pre-requisites of SQL server.
By developing the script based way of creating the certs, it is just at the run of a command we will get the SSL self-signed certificates created and ready to be registered. Along with the creation of the certificate, this blog also explains the different ways of registering those certificates.
Scenario 1:
I will be creating a SSL self-signed certificate using the following 3 methods:
- Using Makecert util from the SDK.
- Using certreq command and a script.sine
- Using powershell command.
Steps to be followed:
- Using Makecert util:
- Firstly, the pre-requisite for using this method is to have Windows SDK installed on the machine.
- Navigate to the location where you have the makecert util and then Run the below command from elevated CMD prompt:
- Run the following command to create the certificate:
makecert -r -pe -n 'CN=MININT-Q99PLQN.fareast.corp.microsoft.com' -b 10/16/2015 -e 12/01/2020 -eku 1.3.6.1.5.5.7.3.1 -ss my -sr localMachine -sky
exchange -sp 'Microsoft RSA SChannel Cryptographic Provider' -sy 12
- We will have the certificate created under the MMC console --> Certificate snap in --> Local Computer --> Personal section
- As per the parameters specified, the certificate will be created with the following set of specifications:
- The common name of the certificate will be “MININT-Q99PLQN.fareast.corp.microsoft.com” which is the FQDN of the machine.
- The private key will be enabled for exporting.
- Certificate will be created in the Computer account -> Personal -> Certificate store
- Validity period will be 10-16-2015 to 12-01-2020
- The server authentication will be enabled. [eku = 1.3.6.1.5.5.7.3.1]
- Key Spec value will be set to 1. [AT_KEYEXCHANGE will be enabled]
- The algorithm used here for encryption is Microsoft RSA SChannel Cryptographic Provider.
2.Using Certreq command:
- Firstly, we need to save the below script in a text document with a .inf extension.
[Version]
Signature = '$Windows NT$'
[NewRequest]
Subject = 'CN = MININT-Q99PLQN.fareast.corp.microsoft.com'
FriendlyName = test1.contoso.com
MachineKeySet = true
RequestType=Cert
;SignatureAlgorithm = SHA256
KeyLength = 4096
KeySpec = 1
KeyUsage = 0xA0
MachineKeySet = True
Exportable = TRUE
Hashalgorithm = sha512
ValidityPeriod = Years
ValidityPeriodUnits = 10
[EnhancedKeyUsageExtension]
OID=1.3.6.1.5.5.7.3.1
- Navigate to the location where you have saved this request.inf file and then Run the below command from elevated CMD prompt
Certreq -new -f .inf .cer
Just dance 2017 activation key generator. Sadly didn’t find anyone to give away the just dance 2019 redeem code. We also did a lot of searches over the internet on this game download. No wonder in that, because it is difficult to collect these expensive codes.
- We will have the certificate created under the MMC console --> Certificate snap in --> LocalComputer --> Personal section
- The advantages of this technique is that it does not require the Windows SDK installed and the key length can be subjected to changes where as if it is using makecert it would be by defaultset to '2048' for 'RSA' and '512' for 'DSS'
3.Using Power-shell command
- Here is the approach to create the SSL certificate satisfying the pre-requisites to load it for SQL server using the power-shell command.
- Run Powershell as an administrator and enter the following command (where DnsName = Host name or FQDN of the machine)
New-SelfSignedCertificate -DnsName MININT-Q99PLQN.fareast.corp.microsoft.com -CertStoreLocation cert:LocalMachineMy -FriendlyName test99 -KeySpec KeyExchange
Scenario: 2
I will be registering the SSL self-signed certificate using the following 2 methods:
- Through the SQL Server Configuration Manager
- Through explicit registration
Steps to be followed:
- Through SQL Server Configuration Manager:
- Initially need to check the health of the certificate using the CheckSQLssl.exe tool.
- Here are the pre-requisites for the SSL certificate to use it for SQL server:
- Certificate must be present in the Local computer certificate store or the current user certificate store.
- Certificate age must be present within the validity period.
- Certificate must be meant for server authentication. (EKU should specify Server Authentication [1.3.6.1.5.5.7.3.1])
- Certificate must be created using the KEY_SPEC option of AT_KEYEXCHANGE (KEY_SPEC=1)
- Common name of the certificate should be the host name or the FQDN of the server computer.
- Running the tool using the command prompt will generate the following report
- On getting all the validation checks ‘OK’ regarding the pre-requisites of the certificate we can go ahead register it.
- On SSCM, expand SQL server network configuration -> Right click on ‘Protocols for <Instance name> -> Properties. Turn the ‘Forced Encryption’ to Yes.
- Click on the ‘Certificate’ tab where the certificates will be listed and select the required certificate from the list and restart the service.
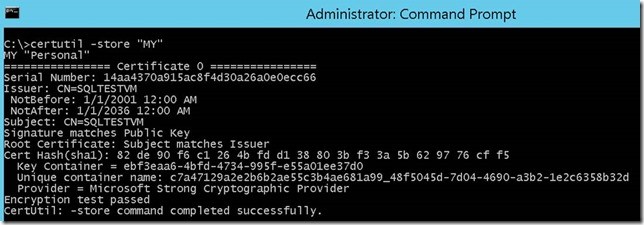
- Thus the SSL certificate will be loaded to the selected SQL server and this can be verified by analyzing the SQL error logs for the below message and verifying it with the thumbprint of the certificate in MMC.
The certificate [Cert Hash(sha1) 'BFB714872C7B2CD761ADEB1893BFC99581D3420B'] was successfully loaded for encryption.
- To verify the thumbprint, in MMC double click on the certificate which is loaded, click on ‘Details’ tab and click on thumbprint in the list.
2.Through explicit registration:
- Even after the validation checks are proved to be OK by the CheckSQLssl tool and still if the certificate is not listed in SSCM, then follow this technique.
- Run ‘regedit’ and open HKEY_LOCAL_MACHINESOFTWAREMicrosoftMicrosoft SQL ServerMSSQL12.MSSQLSERVERMSSQLServerSuperSocketNetLib and enter the thumbprint of the certificate without spaces to the ‘Certificate’ value.
- Note that in case of a clustered environment in those nodes whose FQDN does not match with the certificate name, the certificate will not be listed in the configuration manager. In that case explicit registration is the only way to register the certificate.
- Then on restarting the SQL service the SSL certificate will be loaded to SQL and this can be verified again by analyzing the SQL server error logs.
Written by:
Shreyas R, Support Engineer, SQL Server Support
Reviewed by:
Sravani Saluru, Support Escalation Engineer, SQL Server Support
Pradeep M M, Escalation Engineer, SQL Server Support
-->SQL Server uses encryption keys to help secure data, credentials, and connection information that is stored in a server database. SQL Server has two kinds of keys: symmetric and asymmetric. Symmetric keys use the same password to encrypt and decrypt data. Asymmetric keys use one password to encrypt data (called the public key) and another to decrypt data (called the private key).
In SQL Server, encryption keys include a combination of public, private, and symmetric keys that are used to protect sensitive data. The symmetric key is created during SQL Server initialization when you first start the SQL Server instance. The key is used by SQL Server to encrypt sensitive data that is stored in SQL Server. Public and private keys are created by the operating system and they are used to protect the symmetric key. A public and private key pair is created for each SQL Server instance that stores sensitive data in a database.
Applications for SQL Server and Database Keys
SQL Server has two primary applications for keys: a service master key (SMK) generated on and for a SQL Server instance, and a database master key (DMK) used for a database.
Service master key
The Service Master Key is the root of the SQL Server encryption hierarchy. The SMK is automatically generated the first time the SQL Server instance is started and is used to encrypt a linked server password, credentials, and the database master key. The SMK is encrypted by using the local machine key using the Windows Data Protection API (DPAPI). The DPAPI uses a key that is derived from the Windows credentials of the SQL Server service account and the computer's credentials. The service master key can only be decrypted by the service account under which it was created or by a principal that has access to the machine's credentials.
The Service Master Key can only be opened by the Windows service account under which it was created or by a principal with access to both the service account name and its password.
SQL Server 2019 (15.x) uses the AES encryption algorithm to protect the service master key (SMK) and the database master key (DMK). AES is a newer encryption algorithm than 3DES used in earlier versions. After upgrading an instance of the Database Engine to SQL Server 2019 (15.x) the SMK and DMK should be regenerated in order to upgrade the master keys to AES. For more information about regenerating the SMK, see ALTER SERVICE MASTER KEY (Transact-SQL) and ALTER MASTER KEY (Transact-SQL).
Sql Server Hash Column
Database master key
The database master key is a symmetric key that is used to protect the private keys of certificates and asymmetric keys that are present in the database. It can also be used to encrypt data, but it has length limitations that make it less practical for data than using a symmetric key. To enable the automatic decryption of the database master key, a copy of the key is encrypted by using the SMK. It is stored in both the database where it is used and in the master system database.
The copy of the DMK stored in the master system database is silently updated whenever the DMK is changed. However, this default can be changed by using the DROP ENCRYPTION BY SERVICE MASTER KEY option of the ALTER MASTER KEY statement. A DMK that is not encrypted by the service master key must be opened by using the OPEN MASTER KEY statement and a password.
Managing SQL Server and Database Keys
Managing encryption keys consists of creating new database keys, creating a backup of the server and database keys, and knowing when and how to restore, delete, or change the keys.
To manage symmetric keys, you can use the tools included in SQL Server to do the following:
Back up a copy of the server and database keys so that you can use them to recover a server installation, or as part of a planned migration.
Restore a previously saved key to a database. This enables a new server instance to access existing data that it did not originally encrypt.
Delete the encrypted data in a database in the unlikely event that you can no longer access encrypted data.
Re-create keys and re-encrypt data in the unlikely event that the key is compromised. As a security best practice, you should re-create the keys periodically (for example, every few months) to protect the server from attacks that try to decipher the keys.
Add or remove a server instance from a server scale-out deployment where multiple servers share both a single database and the key that provides reversible encryption for that database.
Important Security Information
Accessing objects secured by the service master key requires either the SQL Server Service account that was used to create the key or the computer (machine) account. That is, the computer is tied to the system where the key was created. You can change the SQL Server Service account or the computer account without losing access to the key. However, if you change both, you will lose access to the service master key. If you lose access to the service master key without one of these two elements, you be unable to decrypt data and objects encrypted by using the original key.
Connections secured with the service master key cannot be restored without the service master key.
Access to objects and data secured with the database master key require only the password that is used to help secure the key.
Caution
If you lose all access to the keys described earlier, you will lose access to the objects, connections, and data secured by those keys. You can restore the service master key, as described in the links that are shown here, or you can go back to the original encrypting system to recover the access. There is no 'back-door' to recover the access.
In This Section
Service Master Key
Provides a brief explanation for the service master key and its best practices.
Extensible Key Management (EKM)
Explains how to use third-party key management systems with SQL Server.
Sql Server Hash Function
Related Tasks
Related Content
Sql Server Hash Password
See Also
Set Length Hash Key Generator Sql Server 2017
Back Up and Restore Reporting Services Encryption Keys
Delete and Re-create Encryption Keys (SSRS Configuration Manager)
Add and Remove Encryption Keys for Scale-Out Deployment (SSRS Configuration Manager)
Transparent Data Encryption (TDE)