Key Generation Process Of Textbook Rsa Algorithym
Key generation is the process of generating keys in cryptography. A key is used to encrypt and decrypt whatever data is being encrypted/decrypted.
- Rsa Key Generation Algorithm
- Key Generation Process Of Textbook Rsa Algorithm 2017
- Example Of Rsa Algorithm
RSA (cryptosystem) RSA (Rivest–Shamir–Adleman) is one of the first public-key cryptosystems and is widely used for secure data transmission. In such a cryptosystem, the encryption key is public and it is different from the decryption key which is kept secret (private). RSA algorithm (Rivest-Shamir-Adleman): RSA is a cryptosystem for public-key encryption, and is widely used for securing sensitive data, particularly when being sent over an insecure network such.
Introduction Textbook RSA Attacks on RSA Padded RSA Textbook RSA Construction 11.26. Define a public-key encryption scheme using GenRSA as follows:. Gen: On input 1n run GenRSA(1n) to obtain N,e and d. The public key is hN,ei and the private key is hN,di. Enc: On input a public key pk = hN,ei and a message m 2 Z ⇤ N, compute the ciphertext.
A device or program used to generate keys is called a key generator or keygen.
Generation in cryptography[edit]
Modern cryptographic systems include symmetric-key algorithms (such as DES and AES) and public-key algorithms (such as RSA). Symmetric-key algorithms use a single shared key; keeping data secret requires keeping this key secret. Public-key algorithms use a public key and a private key. The public key is made available to anyone (often by means of a digital certificate). A sender encrypts data with the receiver's public key; only the holder of the private key can decrypt this data.
Since public-key algorithms tend to be much slower than symmetric-key algorithms, modern systems such as TLS and SSH use a combination of the two: one party receives the other's public key, and encrypts a small piece of data (either a symmetric key or some data used to generate it). The remainder of the conversation uses a (typically faster) symmetric-key algorithm for encryption.
Windows 8.1 activation keys generator. Mar 10, 2020 Windows 8, 8.1 key Generator + Serial Key Free For you. Windows 8.1 Product Key Generator works by utilizing the Key Management System. With a specific end goal to live away from sadness, everybody has to make use of Windows Activator. Which has an extremely plain as day name; it will actuate your windows inside the count number of minutes. Jan 12, 2020 Window 8.1 Activation keys. Window 8.1 Activation Key released after the Windows 8. In this form of Windows, bugs and errors are fixed, and updates that are new been install. This type of Windows supplies a single screen that is well that is graphical. How Do You Activate a Windows 8.1 Product Key Generator Close all the programs. Click the start button, then the Run application should be open. A window of dialogue box will pop up and a text box will appear with this dialogue box. ‘slui 2’ text should be entered. A window asking for the.
Rsa Key Generation Algorithm
Computer cryptography uses integers for keys. In some cases keys are randomly generated using a random number generator (RNG) or pseudorandom number generator (PRNG). A PRNG is a computeralgorithm that produces data that appears random under analysis. PRNGs that use system entropy to seed data generally produce better results, since this makes the initial conditions of the PRNG much more difficult for an attacker to guess. Another way to generate randomness is to utilize information outside the system. veracrypt (a disk encryption software) utilizes user mouse movements to generate unique seeds, in which users are encouraged to move their mouse sporadically. In other situations, the key is derived deterministically using a passphrase and a key derivation function.
Many modern protocols are designed to have forward secrecy, which requires generating a fresh new shared key for each session.
Classic cryptosystems invariably generate two identical keys at one end of the communication link and somehow transport one of the keys to the other end of the link.However, it simplifies key management to use Diffie–Hellman key exchange instead.
The simplest method to read encrypted data without actually decrypting it is a brute-force attack—simply attempting every number, up to the maximum length of the key. Therefore, it is important to use a sufficiently long key length; longer keys take exponentially longer to attack, rendering a brute-force attack impractical. Currently, key lengths of 128 bits (for symmetric key algorithms) and 2048 bits (for public-key algorithms) are common.
Generation in physical layer[edit]

Wireless channels[edit]
A wireless channel is characterized by its two end users. By transmitting pilot signals, these two users can estimate the channel between them and use the channel information to generate a key which is secret only to them.[1] The common secret key for a group of users can be generated based on the channel of each pair of users.[2]
If the user double-taps anywhere on the screen, thefocused action is performed.For guidance on enhancing the accessibility of your Android app, refer to the. You may alsowish to refer to the reference documentation for specific details of classesand methods. AccessibilityThe Maps SDK for Android includes built-in support for accessibility.This section contains a high-level summary of the accessibility features thatare automatically enabled for any application using the API.When users enable the TalkBack accessibility feature on their mobile devices,each single swipe across the screen moves the focus from one UI element to thenext. Generate key for google maps api v2. (An alternative to single swiping is to explore UI elements by dragging afinger over the interface.) As a UI element comes into focus, TalkBack reads outthe name of the element. In particular, it's goodpractice to add an announcement describing the map.
Key Generation Process Of Textbook Rsa Algorithm 2017
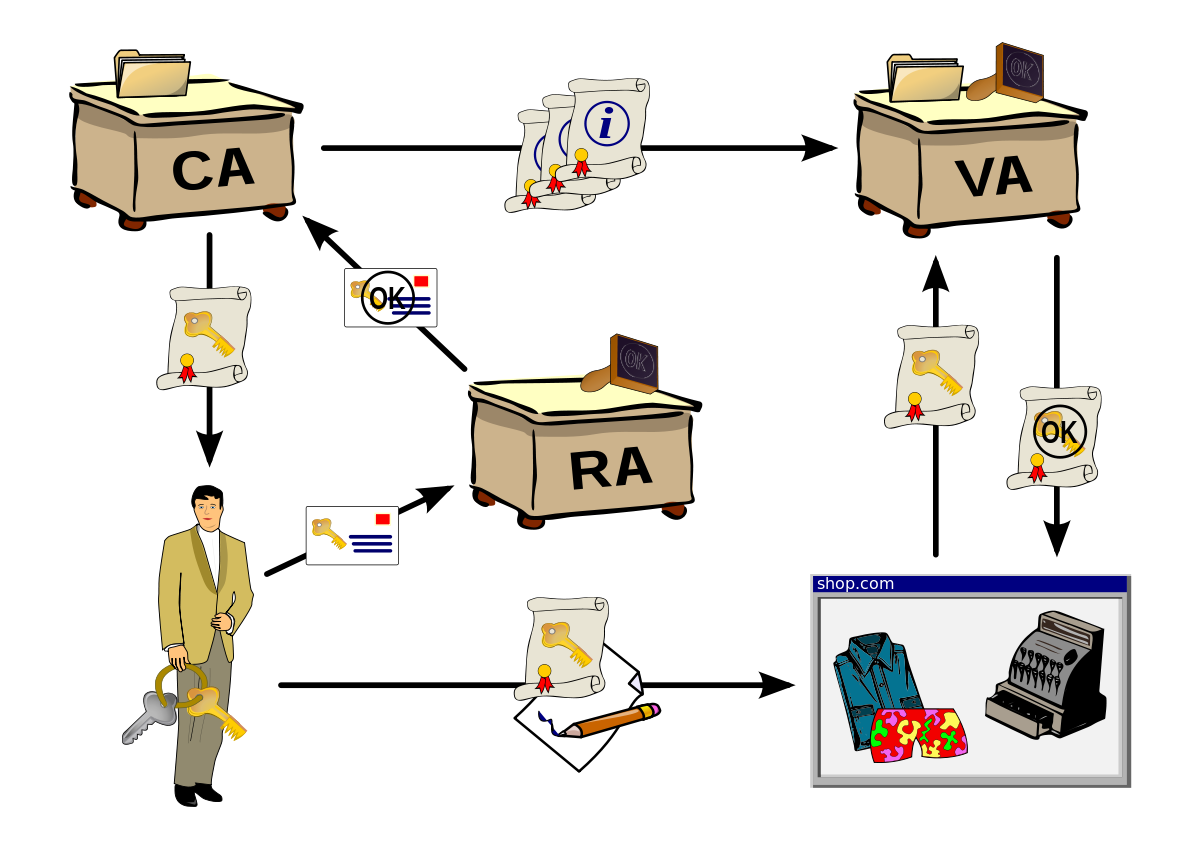
Optical fiber[edit]
A key can also be generated by exploiting the phase fluctuation in a fiber link.[clarification needed]
See also[edit]
- Distributed key generation: For some protocols, no party should be in the sole possession of the secret key. Rather, during distributed key generation, every party obtains a share of the key. A threshold of the participating parties need to cooperate to achieve a cryptographic task, such as decrypting a message.
Example Of Rsa Algorithm
References[edit]
- ^Chan Dai Truyen Thai; Jemin Lee; Tony Q. S. Quek (Feb 2016). 'Physical-Layer Secret Key Generation with Colluding Untrusted Relays'. IEEE Transactions on Wireless Communications. 15 (2): 1517–1530. doi:10.1109/TWC.2015.2491935.
- ^Chan Dai Truyen Thai; Jemin Lee; Tony Q. S. Quek (Dec 2015). 'Secret Group Key Generation in Physical Layer for Mesh Topology'. 2015 IEEE Global Communications Conference (GLOBECOM). San Diego. pp. 1–6. doi:10.1109/GLOCOM.2015.7417477.