Generate Ssh Public Key Mac Os X
This will step you through the process of generating a SSH keypair on Mac OS X. Begin by opening your Terminal, generally found in the 'Utilities' subdirectory of your 'Applications' directory. Generating a keypair. Before you generate your keypair, come up with a passphrase. The rules for good passwords also apply here: mix of upper and lower case, numbers, spaces and punctuation.
You generate an SSH key through Mac OS X by using the Terminal application. Once you upload a valid public SSH key,Gerrit can authenticate you based on this key.
Generating a Keypair Adding Your Public Key to Launchpad More In Depth Example Linux and Mac OS X both come with support for SSH and SSH keys out of the box. Launchpad uses SSH keys to authenticate your computer with your Launchpad account. This guide shows you how to get that done. To generate SSH keys in Mac OS X, follow these steps: Enter the following command in the Terminal window: ssh-keygen -t rsa -b 4096. This starts the key generation process. When you execute this command, the ssh-keygen utility prompts you to indicate where to store the key. Oct 23, 2017 How To: Create SSH Remote Login Mac OS X and Force Private Key Authentication Only - Putty. Open idrsa.pub and copy the text into your authorizedkeys file. Save the file. Download and install PuttyGen here. Save private key. Click Yes to save without a password (this is not.
An SSH key consists of a pair of files. One is the private key, which you should never give to anyone. No one will everask you for it and if so, simply ignore them - they are trying to steal it.The other is the public key. When you generate your keys, you will use ssh-keygen to store the keys in a safe locationso you can authenticate with Gerrit.
To generate SSH keys in Mac OS X, follow these steps:
Enter the following command in the Terminal window:
This starts the key generation process. When you execute this command, the ssh-keygen utility prompts you to indicate where to store the key.
Press the
ENTERkey to accept the default location. The ssh-keygen utility prompts you for a passphrase.Type in a passphrase. You can also hit the
ENTERkey to accept the default (no passphrase). However, this is not recommended.
Warning
You will need to enter the passphrase a second time to continue.
After you confirm the passphrase, the system generates the key pair and you will see output like this:
Generate Ssh Public Key Mac Os X 10 7 Download Free
Your private key is saved to the id_rsa file in the .ssh subdirectory of your home directory and is used to verifythe public key you use belongs to your Gerrit account.
Warning
Never share your private key with anyone! Ever! We mean it!
Your public key is saved to a file called id_rsa.pub in the .ssh subdirectory of your home directory. You can copyit to your clipboard using the following command:
Now you can head over to Gerrit, go to settings and paste your public key as described here.
Gerrit is using the special port 29418 instead of the default SSH port 22 which has to be configured accordingly. This can be done in your local ~/.ssh/config file which would contain the following sections then:
Testing your connection:
This guide goes through setting up SSH keys on macOS Mojave 10.14 back to Mac OSX 10.11 and also a secure password-less SSH connection between a local macOS workstation and a remote server also running a Linux variant operating system.
Generate Ssh Key Osx
The process requires generating a public and private key on the local computer and then adding the public key to the remote servers authorised list. What is great about this is that it allows a password prompt free session, handy for a lot of uses.
First thing that you need to do on your macOS machine is to create a directory that will store your SSH keys. Then you will generate a public and private key for your account, launch the Terminal and punch in some commands:
Create a .ssh Directory
Change to the home directory
Create a SSH directory name .ssh and move into it
Make sure that the file permissions are set to read/write/execute only for the user
Create your private and public key, the blank quotes at the end of the command gives the private key no password, so allowing for passwordless logins!
Change into the .ssh directory and list the contents of that .ssh directory
$ chmod 400 MyKeyPair.pem Display Your Key PairA 'fingerprint' is generated from your key pair, and you can use it to verify thattheprivate key that you have on your local machine matches the public key that's storedin AWS.The fingerprint is an SHA1 hash taken from a DER-encoded copy of the private key.Thisvalue is captured when the key pair is created, and is stored in AWS with the publickey.You can view the fingerprint in the Amazon EC2 console or by running the AWS CLI commandawsec2 describe-key-pairs.The following example displays the fingerprint for MyKeyPair. Aws create ssh key pair.
Thats your SSH keys created, the private key is the id_rsa and the public one is the id_rsa.pub, don’t give out the private one always keep that one only on your local machine.
Sharing the Public Key
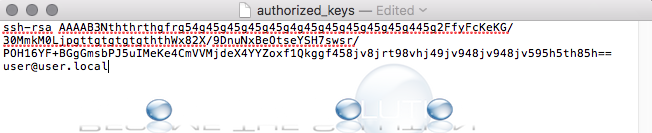
Create an authorized_keys in the .ssh directory of the remote computer that you want to connect to.
You can create automatic logins by adding the contents of your public key to the authorized_keys file on the remote device.
To see and copy your public key use the cat command and copy the contents:
On the remote computer if needed, change the permssions on the authorized_keys file to write to add the public key, on a new line paste in your public key, and change permissions back to read only after for security.
Allow write on authorised_keys
Paste the entire id_rsa.pub content with vi or nano into the authorized_keys file, if using nano use the -w flag to not use incorrect line breaks.
If the remote host does not have an “authorized_keys” file simply create one and after the public key is pasted in don’t forget to takeaway write permissions.
Going Both Ways
So now when you connect via SSH no password is prompted as the remote computer has your public key which is only decrypted by your private key held in your local .ssh/ directory. If you want the communications to be bilateral then repeat the process in the opposite order between the two.
Now the two computers can securely connect with no password prompting, making it ideal to script between the two for file copies or back ups.
Doing it Quicker
Now instead of typing in
Make an alias in your bash shell you could alias it to
Reload the the shell
Then all you have to type in is the alias