Generate Google Ajax Api Key
- Jun 11, 2019 Introduction. This document is intended for developers who want to write applications that can interact with the Blogger JSON API. Blogger is a tool for creating websites that allow people to publish their thoughts on an ongoing basis.
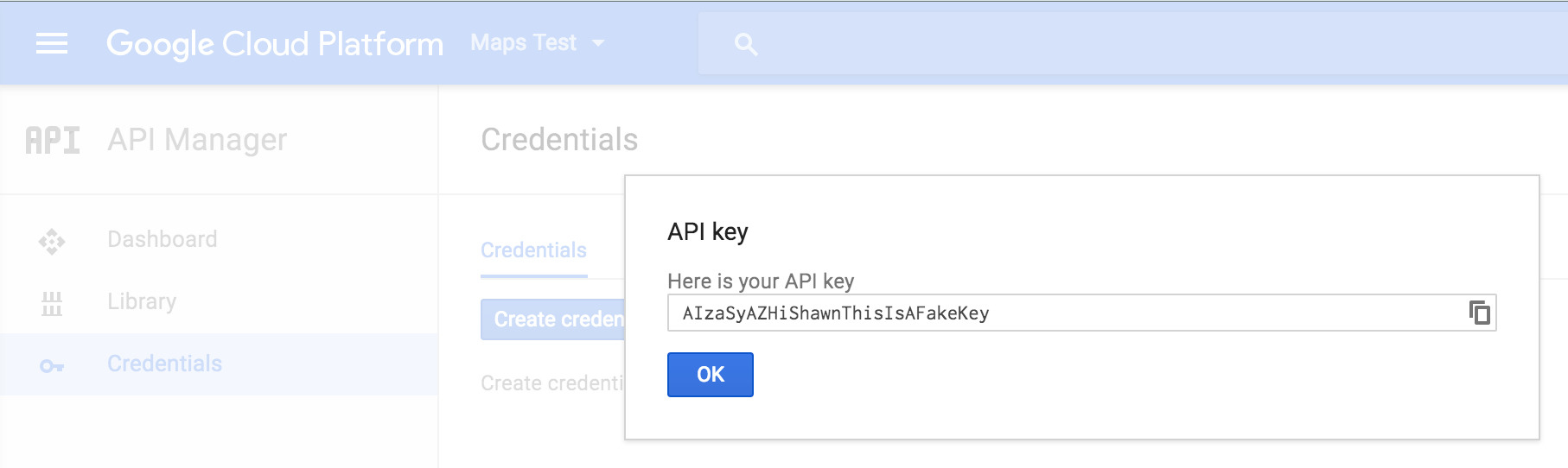
- Apr 10, 2020 To get an API key: Go to the Google Cloud Platform Console. Click the project drop-down and select or create the project for which you want to add an API key. Click the menu button and select APIs & Services Credentials. On the Credentials page, click Create credentials API key. The API key created dialog displays your newly created API key.
- REST authentication and exposing the API key. Ask Question Asked 9 years ago. I'd have to embed the api key in the ajax call so that it gets passed to the server.at that point someone can see the API key. Create a CSRF token from the API key and the random value from the cookie, and sign it. (Rather than keeping a list of tokens on.
- These instructions apply for non Google Cloud Platform (GCP) APIs. If you're building a GCP application, see using API keys for GCP. If your client application does not use OAuth 2.0, then it must include an API key when it calls an API that's enabled within a Google Cloud Platform project.
This document describes how to use the common features of the Blogger JSON API using the RESTful calling style.
How to use an API Key for an Ajax call? I am trying to include an API key for the first time from New York Times API. Sign up using Google.
Contents
- Introduction
- Working with Blogs
- Working with Posts
- Working with Comments
- Working with Pages
- Working with Users
Introduction
This document is intended for developers who want to write applications thatcan interact with the Blogger JSON API. Blogger is a tool forcreating websites that allow people to publish their thoughts on an ongoingbasis.
If you're unfamiliar with Blogger concepts, you should read Getting Started before starting to code.
Authorizing requests and identifying your application
Every request your application sends to the Blogger JSON API needs toidentify your application to Google. There are two ways to identify yourapplication: using an OAuth 2.0 token (whichalso authorizes the request) and/or using the application's API key. Here's how to determine which of those options touse:
Windows Anytime Upgrade Key Free Office, Windows Comments: 0 Upgrade to Windows 7 Ultimate with Anytime Upgrade – TechRepublic If you have lost your Windows 7 product key then you can follow these methods to find it- 1- Look for it in the Sticker provided on your PC If you have purchased your laptop or PC with pre-installed. VIDEO: Windows Anytime Upgrade Key Generator Windows 10 can be one of the most beautiful operating system Microsoft have created apart from windows which was also very lovely. Windows Anytime Upgrade feature in Windows 7 allows users to upgrade their already installed operating-system into higher versions letting. Feb 25, 2020 Windows 8.1 Product Key undoubtedly is an awaited upgrade to Windows 8. It is designed to overcome all the problems that Windows 8 users suffered. This advanced upgrade includes almost every new feature and functions. It allows us to transform overall user-experience on Microsoft OS. Windows 8 professional product key is a 25-digit character code used to activate a copy of Windows 8 professional. Without a working pro activation key, you will not be able to activate the Operating System. Windows 10 key generator download.
- If the request requires authorization (such as a request for an individual's private data), then the application must provide an OAuth 2.0 token with the request. The application may also provide the API key, but it doesn't have to.
- If the request doesn't require authorization (such as a request for public data), then the application must provide either the API key or an OAuth 2.0 token, or both—whatever option is most convenient for you.
About authorization protocols
Your application must use OAuth 2.0to authorize requests. No other authorization protocols are supported.
Note: The Blogger JSON API does not currently support loggingin at the same time as requesting data access (hybrid) or domain-widedelegation of authority (2LO).
Authorizing requests with OAuth 2.0
Requests to the Blogger JSON API for non-public user data must be authorizedby an authenticated user.
The details of the authorization process, or 'flow,' for OAuth 2.0 varysomewhat depending on what kind of application you're writing. The followinggeneral process applies to all application types:
- When you create your application, you register it with Google. Google then provides information you'll need later, such as a client ID and a client secret.
- Activate the Blogger JSON API in the Services pane of the Google APIs Console. (If it isn't listed in the Console, then skip this step.)
- When your application needs access to user data, it asks Google for a particular scope of access.
- Google displays an OAuth dialog to the user, asking them to authorize your application to request some of their data.
- If the user approves, then Google gives your application a short-lived access token.
- Your application requests user data, attaching the access token to the request.
- If Google determines that your request and the token are valid, it returns the requested data.
Some flows include additional steps, such as using refresh tokens to acquire new access tokens. For detailed information aboutflows for various types of applications, see Google's OAuth 2.0 documentation.
Here's the OAuth 2.0 scope information for theBlogger JSON API:
To request access using OAuth 2.0, your application needs the scopeinformation, as well as information that Google supplies during applicationregistration (such as the client ID and/or the client secret).
Tip: The Google APIs client libraries canhandle some of the authorization process for you. They are available for avariety of programming languages; check the Libraries and Samples page formore details.
Acquiring and using an API key
Requests to the Blogger JSON API for public data must be accompanied by anidentifier, which can be an API key or an auth token.
To acquire an API key, visit the APIs Console. In the Servicespane, activate the [api_name]; if the Terms of Service appear, read and acceptthem.
Next, go to the API Access pane. The API key is near the bottom of that pane, in the sectiontitled 'Simple API Access.'
After you have an API key, your application can append the query parameterkey=yourAPIKey to all requestURLs.
The API key is safe for embedding in URLs; it doesn't need any encoding.
Working with Blogs
Retrieving a Blog
You can retrieve information for a particular Blogs Resource by sending an HTTPGET request to the Blog's URI. The URI for a Blogs Resource has the following format:
Request
Here is an example:
Since a user does not have to be authenticated to retrieve a public Blog, youdon't have to provide the Authorization HTTP header with thisGET request; but if you don't provide that header, then you do need to provide an API key.
Blogger also has private Blogs, which do requireauthentication.
Response
If the request succeeds, the server responds with an HTTP200 OK status code and the blog data:
Retrieving a User's Blogs
You can retrieve a list of a user's blogs by sending an HTTP GET requestto the Blogs Collection URI:
Request
Here is an example of a GET request that lists auser's blogs:
Note: The user must be authenticated tolist their own blogs, so you must provide the Authorization HTTPheader with the GET request.
Response
If the request succeeds, the server responds with an HTTP200 OK status code and the full representation of the list of the user'sblogs:
Working with Posts
Retrieving Posts from a Blog
You can retrieve a list of Posts from a given Blog by sending aGET request to the Posts Collection URI. The URI for a PostsCollection has the following format:
Request
Here is an example:
Since a user does not have to be authenticated to retrieve the Posts from a public Blog, youdon't have to provide the Authorization HTTP header with thisGET request; but if you don't provide that header, then you do need to provide an API key.
Blogger also has private Blogs, which do requireauthentication.
Response
If the request succeeds, the server responds with an HTTP200 OK status code and the list of Posts:
Retrieving a Specific Post
You can retrieve a specific Post from a Blog by sending aGET request to the Posts Resource URI. The URI for a PostsResource has the following format:
Request
Here is an example:
Since a user does not have to be authenticated to retrieve the Posts from a public Blog, youdon't have to provide the Authorization HTTP header with thisGET request; but if you don't provide that header, then you do need to provide an API key.
Blogger also has private Blogs, which do requireauthentication.
Response
If the request succeeds, the server responds with an HTTP200 OK status code and the contents of the Post:
Working with Comments
Retrieving Comments for a Post
You can retrieve a list of Comments for a Post by sending aGET request to the Comments Collection URI. The URI for aComments Collection has the following format:
Request
Generate Google Ajax Api Key Finder
Here is an example:
Since a user does not have to be authenticated to retrieve the Comments from a public Blog, youdon't have to provide the Authorization HTTP header with thisGET request; but if you don't provide that header, then you do need to provide an API key.
Blogger also has private Blogs, which do requireauthentication.
Response
If the request succeeds, the server responds with an HTTP200 OK status code and the list of comments:
Retrieving a Specific Comment
You can retrieve a specific Comment from a Post by sending aGET request to the Comments Resource URI. The URI for aComments Resource has the following format:
Request
Here is an example:
Since a user does not have to be authenticated to retrieve the Comments from a public Blog, youdon't have to provide the Authorization HTTP header with thisGET request; but if you don't provide that header, then you do need to provide an API key.
Blogger also has private Blogs, which do requireauthentication.
Response
If the request succeeds, the server responds with an HTTP200 OK status code and the comment data:
Working with Pages
Retrieving Pages for a Blog
You can retrieve a list of Pages for a Blog by sending aGET request to the Pages Collection URI. The URI for a PagesCollection has the following format:
Request
Here is an example:
Since a user does not have to be authenticated to retrieve the Pages from a public Blog, youdon't have to provide the Authorization HTTP header with thisGET request; but if you don't provide that header, then you do need to provide an API key.
Blogger also has private Blogs, which do requireauthentication.
Response
If the request succeeds, the server responds with an HTTP200 OK status code and the list of Pages:
Retrieving a Specific Page
You can retrieve a specific Page from a Blog by sending aGET request to the Pages Resource URI. The URI for a PagesResource has the following format:
Request
Here is an example:
Since a user does not have to be authenticated to retrieve the Pages from a public Blog, youdon't have to provide the Authorization HTTP header with thisGET request; but if you don't provide that header, then you do need to provide an API key.
Blogger also has private Blogs, which do requireauthentication.
Response
If the request succeeds, the server responds with an HTTP200 OK status code and the page data:
Working with Users
Retrieving a User
You can retrieve a user's information by sending an HTTP GET requestto the Users Resource URI:
Request
Here is an example of a GET request that lists auser's blogs:
Note: The user must be authenticated tolist their own information, so you must provide the Authorization HTTPheader with the GET request.
Response
If the request succeeds, the server responds with an HTTP200 OK status code and a link to a list of the user'sblogs:
Standard query parameters
The following query parameters can be used with all methods and all resources in the Blogger APIs.
Query parameters that apply to all Blogger APIs operations are shown in the table below.
Notes (on API keys and auth tokens):
- The
keyparameter is required with every request, unless you provide an OAuth 2.0 token with the request. - You must send an authorization token with every request that requires an OAuth scope. OAuth 2.0 is the only supported authorization protocol.
- You can provide an OAuth 2.0 token with any request in one of two ways:
- Using the
access_tokenquery parameter like this:?access_token=oauth2-token - Using the HTTP
Authorizationheader like this:Authorization: Beareroauth2-token
- Using the
All parameters are optional except where noted.
| Parameter | Meaning | Notes |
|---|---|---|
access_token | OAuth 2.0 token for the current user. |
|
callback | Callback function. |
|
fields | Selector specifying a subset of fields to include in the response. |
|
key | API key. (REQUIRED*) |
|
prettyPrint | Returns response with indentations and line breaks. |
|
quotaUser | Alternative to userIp. |
|
userIp | IP address of the end user for whom the API call is being made. |
|
When your application requests private data, the request must be authorized by an authenticated user who has access to that data.
When your application requests public data, the request doesn't need to be authorized, but does need to be accompanied by an identifier, such as an API key.
Every request your application sends to the Google Sheets API needs to identify your application to Google. There are two ways to identify your application: using an OAuth 2.0 token (which also authorizes the request) and/or using the application's API key. Here's how to determine which of those options to use:
- If the request requires authorization (such as a request for an individual's private data), then the application must provide an OAuth 2.0 token with the request. The application may also provide the API key, but it doesn't have to.
- If the request doesn't require authorization (such as a request for public data), then the application must provide either the API key or an OAuth 2.0 token, or both—whatever option is most convenient for you.
About authorization protocols
Your application must use OAuth 2.0 to authorize requests. No other authorization protocols are supported. If your application uses Google Sign-In, some aspects of authorization are handled for you.
Authorizing requests with OAuth 2.0
Requests to the Google Sheets API for non-public user data must be authorized by an authenticated user.
The details of the authorization process, or 'flow,' for OAuth 2.0 vary somewhat depending on what kind of application you're writing. The following general process applies to all application types:
- When you create your application, you register it using the Google API Console. Google then provides information you'll need later, such as a client ID and a client secret.
- Activate the Google Sheets API in the Google API Console. (If the API isn't listed in the API Console, then skip this step.)
- When your application needs access to user data, it asks Google for a particular scope of access.
- Google displays a consent screen to the user, asking them to authorize your application to request some of their data.
- If the user approves, then Google gives your application a short-lived access token.
- Your application requests user data, attaching the access token to the request.
- If Google determines that your request and the token are valid, it returns the requested data.
Some flows include additional steps, such as using refresh tokens to acquire new access tokens. For detailed information about flows for various types of applications, see Google's OAuth 2.0 documentation.
Here's the OAuth 2.0 scope information for the Google Sheets API:
| Scope | Meaning |
|---|---|
https://www.googleapis.com/auth/spreadsheets.readonly | Allows read-only access to the user's sheets and their properties. |
https://www.googleapis.com/auth/spreadsheets | Allows read/write access to the user's sheets and their properties. |
https://www.googleapis.com/auth/drive.readonly | Allows read-only access to the user's file metadata and file content. |
https://www.googleapis.com/auth/drive.file | Per-file access to files created or opened by the app. |
https://www.googleapis.com/auth/drive | Full, permissive scope to access all of a user's files. Request this scope only when it is strictly necessary. |
To request access using OAuth 2.0, your application needs the scope information, as well asinformation that Google supplies when you register your application (such as the client ID and theclient secret).
Acquiring and using an API key
Requests to the Google Sheets API for public data must be accompanied by an identifier, which can be an API key or an access token.
To acquire an API key:
- Open the Credentials page in the API Console.
- This API supports two types of credentials. Create whichever credentials are appropriate for your project:
OAuth 2.0: Whenever your application requests private user data, it must send an OAuth 2.0 token along with the request. Your application first sends a client ID and, possibly, a client secret to obtain a token. You can generate OAuth 2.0 credentials for web applications, service accounts, or installed applications.
Gitlab generate ssh key putty. For more information, see the OAuth 2.0 documentation.
API keys: A request that does not provide an OAuth 2.0 token must send an API key. The key identifies your project and provides API access, quota, and reports.
The API supports several types of restrictions on API keys. If the API key that you need doesn't already exist, then create an API key in the Console by clicking Create credentials > API key. You can restrict the key before using it in production by clicking Restrict key and selecting one of the Restrictions.
Generate Api Key
To keep your API keys secure, follow the best practices forsecurely using API keys.
After you have an API key, your application can append the query parameterkey=yourAPIKey to all request URLs.
The API key is safe for embedding in URLs; it doesn't need any encoding.